Introduction
Virtual Private Networks (VPNs) have become a staple tool for privacy, streaming, and secure browsing. But can VPNs themselves be hacked? Unfortunately, yes. While VPNs add layers of encryption and anonymity to your online activity, they are not impervious. In this article, we’ll dive into how VPNs can be compromised, explore real‑world breach cases, explain what makes some VPNs safer than others, and share practical steps to stay protected.
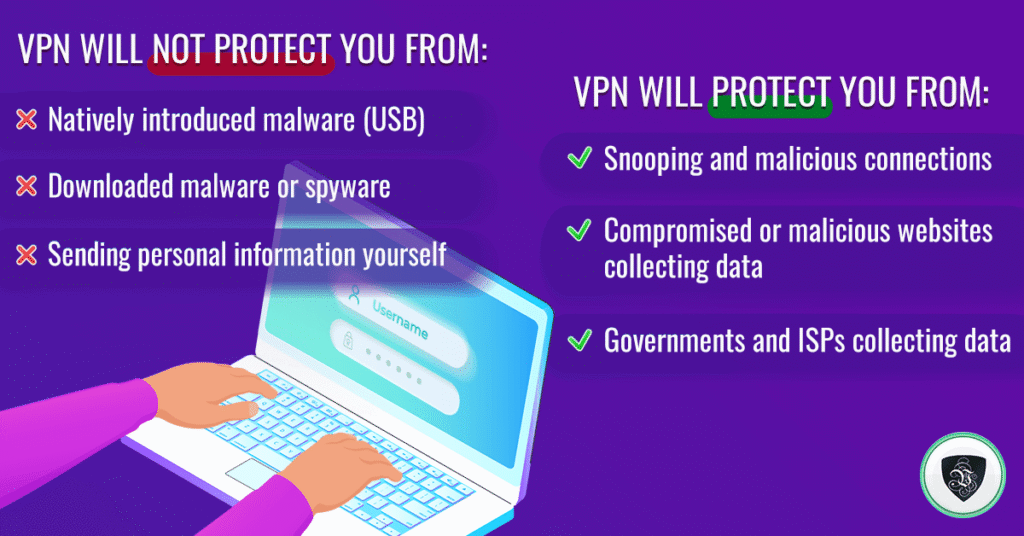
What Is a VPN—and How It Works
VPNs create an encrypted “tunnel” between your device and a VPN server, masking your IP address and routing traffic securely. This guards against eavesdroppers on public Wi‑Fi, ISPs, and location‑based blockers. However, VPNs do not protect devices from malware or physical access—and they rely on solid software and infrastructure to stay secure
Can VPNs Really Be Hacked?
All VPNs are technically hackable—no digital system is infallible. However, well‑maintained, reputable providers make it extremely difficult. Most real attacks stem from:
- Vulnerabilities in VPN client apps or server software
- Weak or outdated encryption or tunneling protocols
- Compromised credentials or infrastructure misconfigurations
- Malicious or fake VPN apps posing as legitimate services


Free VPNs vs Paid VPNs
- Free VPNs often lack security budgets and may include malware, log your data, or sell it—making them vulnerable .
- Paid, audited VPNs (NordVPN, ExpressVPN, Surfshark, etc.) invest heavily in patching, strong encryption like AES‑256 or ChaCha20, and open‑source protocols such as OpenVPN or WireGuard .
Real‑World Examples of VPN Hacks
Ivanti & SonicWall VPN Breaches
In early 2025, a zero‑day vulnerability in Ivanti Connect Secure VPN (CVE‑2025‑0282, ‑0283) was exploited by attackers to breach corporate networks. Similarly, SonicWall SSL VPN appliances were compromised, allowing deployment of Akira ransomware on affected systems .
Pulse Secure Backdoor Campaign
Major penetration of Pulse Secure SSL VPNs led to prolonged espionage across defense and finance sectors. Attackers used stolen credentials to maintain persistent access before patches were widely adopted .
Spyware in Fake VPN Apps
Security researchers recently uncovered DCHSpy, spyware disguised as legit VPNs (e.g. EarthVPN, ComodoVPN) targeting Android users. Once installed, it can harvest messages, files, audio, and location data. GitHub has also become a distribution platform for fake “free VPN” tools that hide malware like Lumma Stealer using ZIP files and DLL injection.
How Are VPNs Hacked? Common Attack Vectors
- Software bugs in client or server code
- Obsolete encryption standards or misconfigured protocols
- Weak credentials or reused passwords
- Social engineering or phishing attacks
- Installing fake VPN apps from untrusted sources
- Man‑in‑the‑Middle (MitM) attacks if certificate validation fails or trusted roots are compromised
Warning Signs Your VPN May Be Compromised
Be alert to indicators such as:
- Unexplained slowdowns or frequent disconnections
- Suspicious app behavior or unexplained permissions
- Alerts from antivirus/endpoint tools
- Credential leak notifications
- Unexpected geolocation reveals or IP changes
Protecting Yourself: VPN Safety Checklist
Choose and use VPNs wisely by following these best practices:
- Use reputable paid VPNs, audited and no‑logs certified (e.g. NordVPN, Surfshark, ExpressVPN)
- Keep VPN apps up to date to apply patches promptly
- Check protocol & encryption: prefer OpenVPN or WireGuard with AES‑256 or ChaCha20
- Enable kill switch & auto‑connect features
- Use strong, unique passwords and enable MFA where possible
- Download apps only from official stores
- Pair VPN usage with endpoint security software
Are All Attacks Rare or Catastrophic?
Most VPN compromises target enterprise-grade infrastructure—not consumer apps. However, spyware-laced fake apps, or breaches of popular VPN appliances, demonstrate that both consumer and corporate users are at risk—especially if they rely on outdated systems or unsafe services.
Summary Table: Potential Threat vs Protection Strategy
| Threat Vector | Risk Level | Recommended Protection |
|---|---|---|
| Client app vulnerability | Medium | Keep apps updated, choose audited providers |
| Server-side zero-day | Low (for users) | Provider-managed patching |
| Fake/malicious VPN apps | High (mobile) | Official app stores + antivirus checks |
| Weak encryption or outdated protocol | Medium | Prefer OpenVPN/WireGuard with modern ciphers |
| Credential reuse or phishing | Medium–High | Use unique credentials + MFA |
| Compromised VPN server provider | Very Low | Select top-tier, transparent VPN providers |
Frequently Asked Questions (FAQ)
- Can using a VPN make me safer from hacking?
Yes—VPNs hide your IP and encrypt traffic, reducing risk from MitM attacks and network surveillance, especially on public Wi‑Fi - Are free VPNs safe?
Generally no. Many lack encryption or privacy policies, and some contain malware or log your data for resale. - Has a major VPN ever been hacked?
Yes—enterprise VPN systems like Ivanti, SonicWall, and Pulse Secure have been breached, typically through zero-day exploits or credential theft. - Can VPN encryption be cracked?
When implemented with strong protocols (AES‑256, ChaCha20, WireGuard), encryption is extremely difficult to break in practice . - How do I know if my VPN is legitimate?
Download only from official stores, verify provider reputation and audit records, review user permissions, and monitor app behavior.
Conclusion
Yes, VPNs can be hacked—but reputable, paid providers make that extremely unlikely. Most risks stem from user error, poor implementations, or malicious imitation. With careful provider selection, secure app usage, strong credentials, and basic digital hygiene, VPNs remain one of the best tools for online privacy and security. Stay informed, update regularly, and avoid dubious VPN apps—then your VPN will continue to be an effective safeguard.








